The Windows 2000 Ipsec setup !
Create a new IPSec Security Policy via a MMC.

Click NEXT.
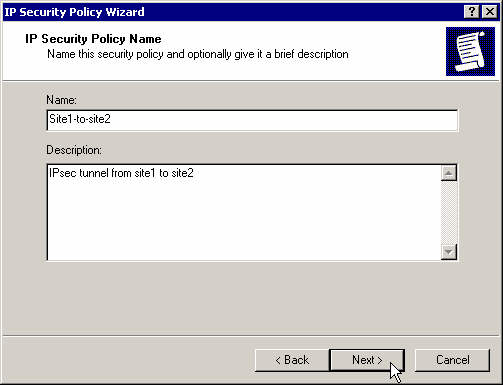
Enter a name for the new policy.
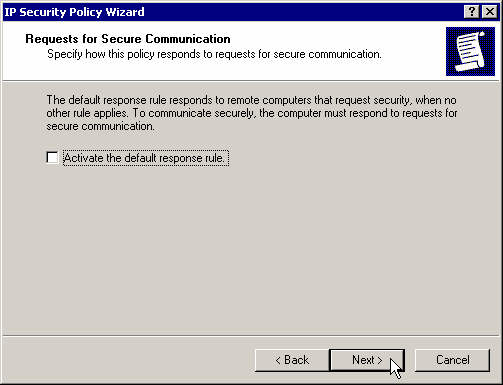
Deactivate the default response rule, NEXT.
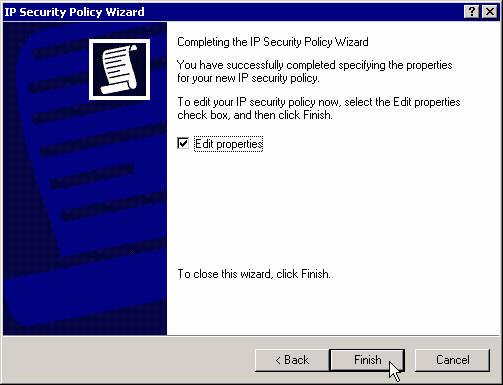
Click Finish.
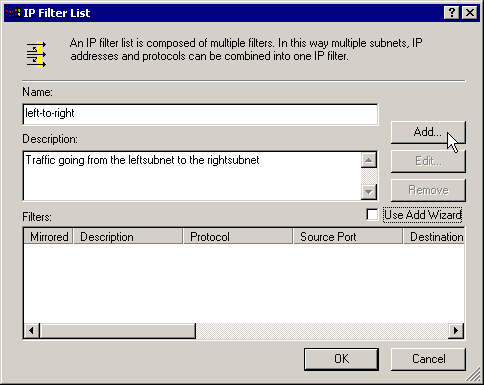
Create the first IP filter for the traffic from the left subnet to the right subnet.
Click ADD.
Enter a name, description and add the filter.
Enter the left subnet as the source address and the right subnet as the destination address.
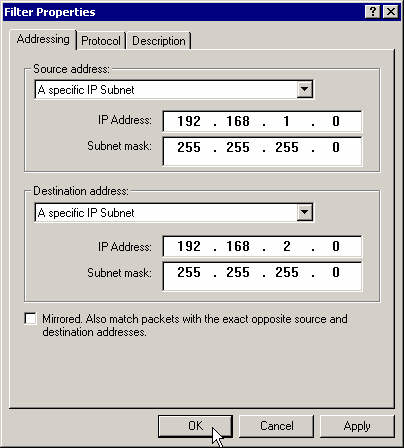
Close that filter's properties box.
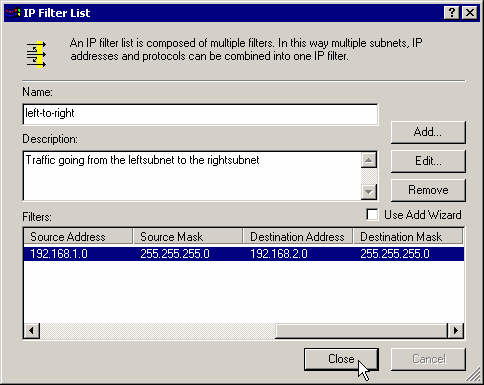
Assign the newly created filter to the current rule.
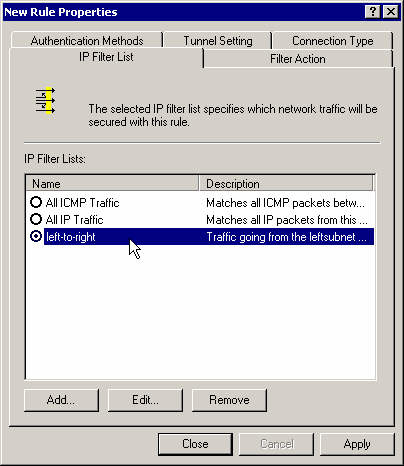
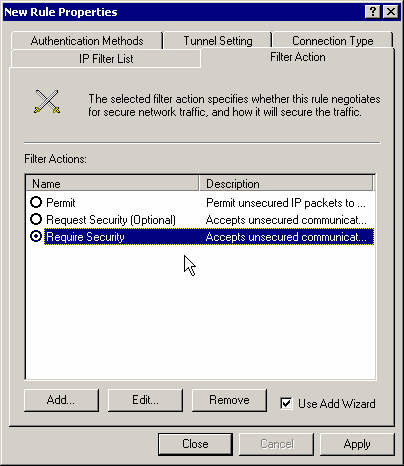
Set the filter action to the Require Security action.
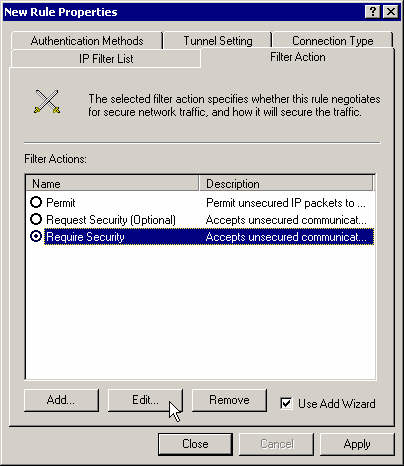
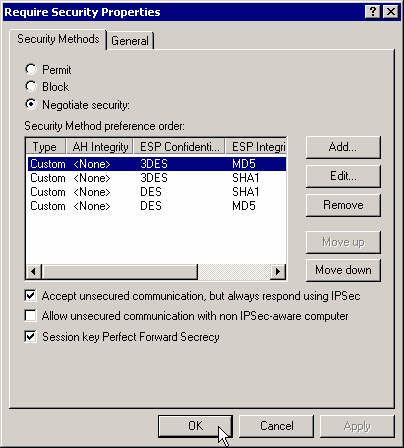
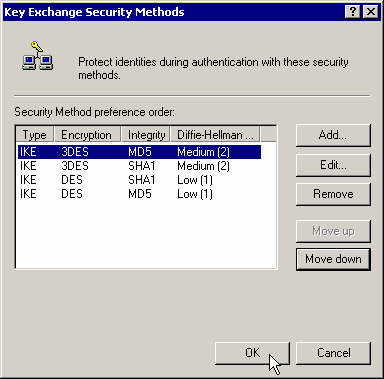
Set this action properties and move the proposal 3DES-MD5 to the top of the list. Select Session Key Perfect Forward Secrecy.
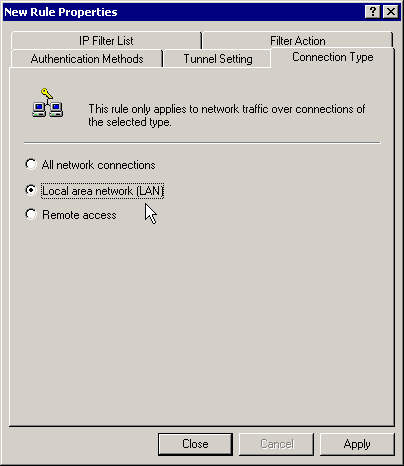
Set the connection's type for a LAN.
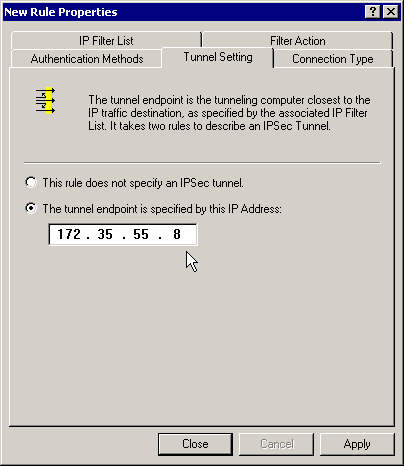
Specify the right gateway IP adress.
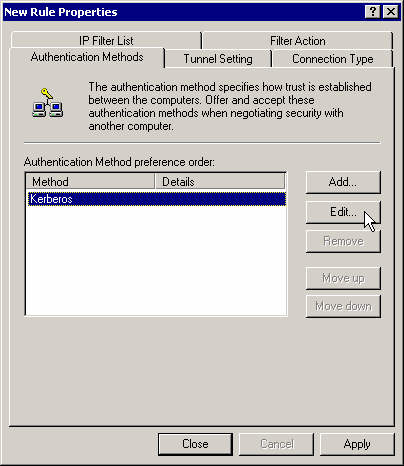
Modify the authentication method.
Set it to preshared key and enter it there.
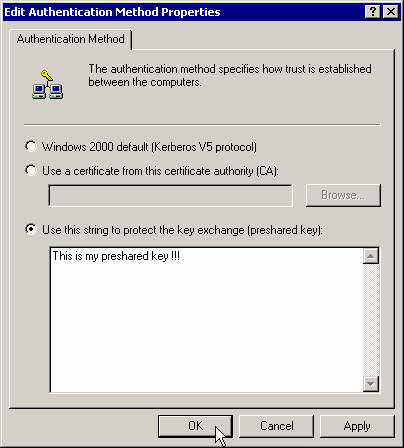
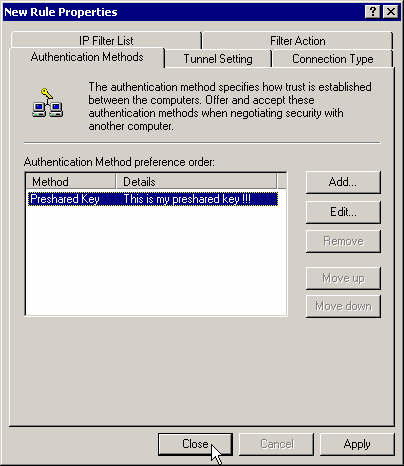
Close the first rule's properties box.
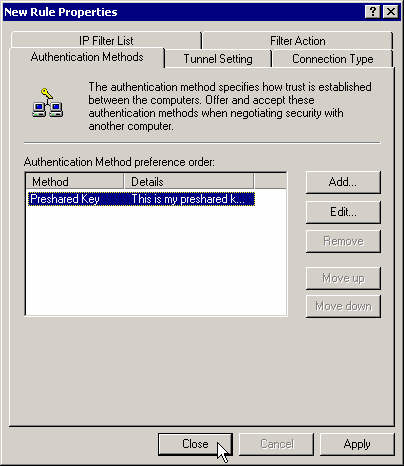
Create a second rule for the traffic from the right subnet to the left subnet.
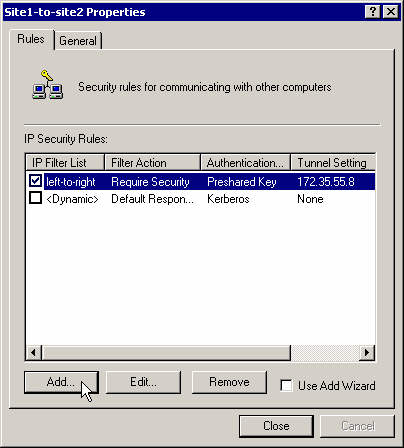
Create a new filter for that rule.
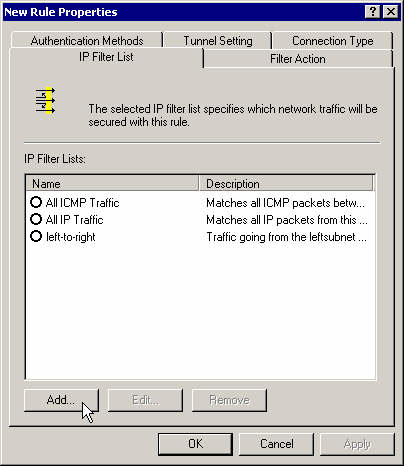
Enter a name, description and add the filter.
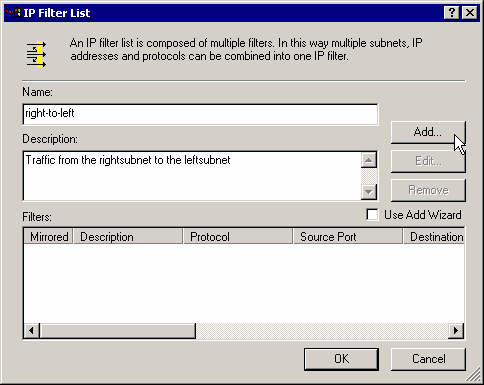
Enter the right subnet as the source address and the left subnet as the destination address.
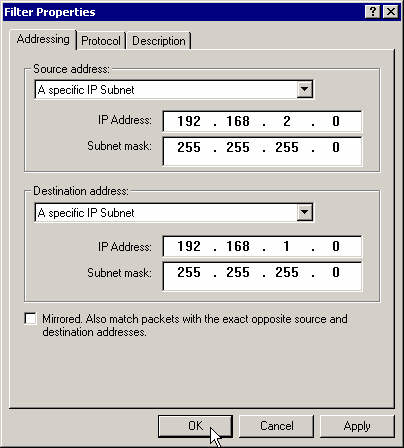
Close the IP filter's properties box.
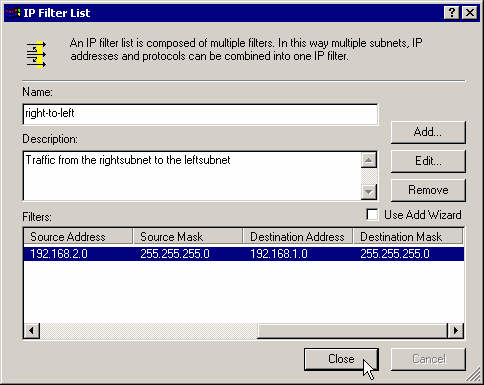
Assign the newly created filter to that rule
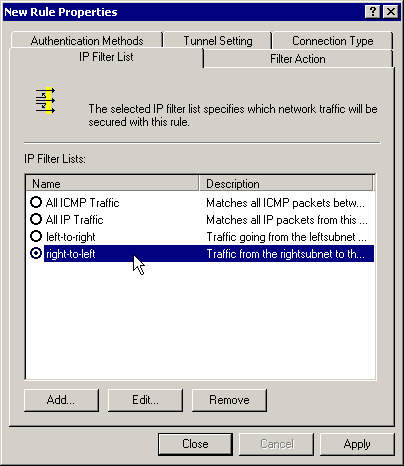
Select the Require Security action (no need to edit it again).
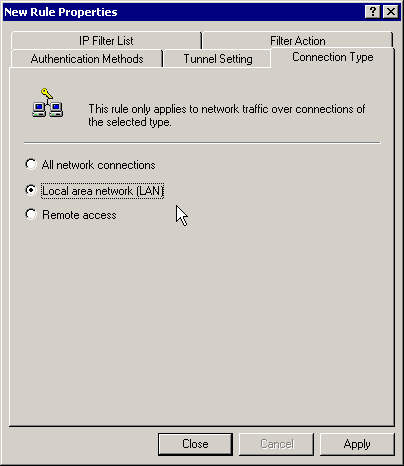
Set the connection's type to LAN.
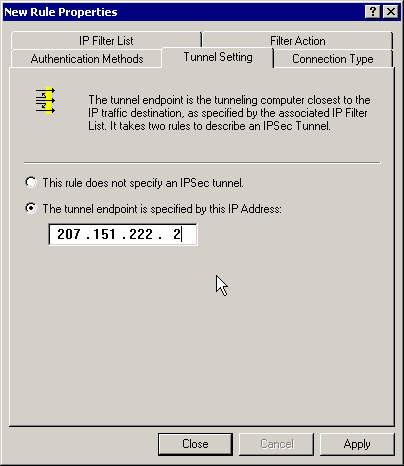
Enter the leftgateway (you !) as the tunnel enpoint.
Modify the authentication method.
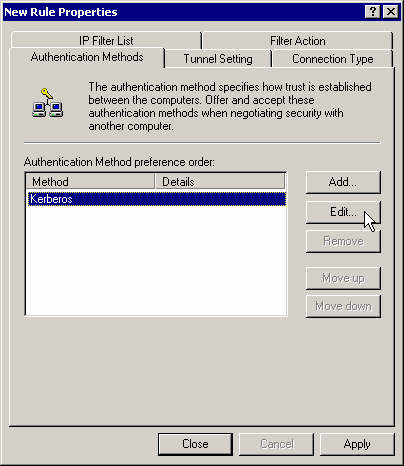
Enter you preshared key again.
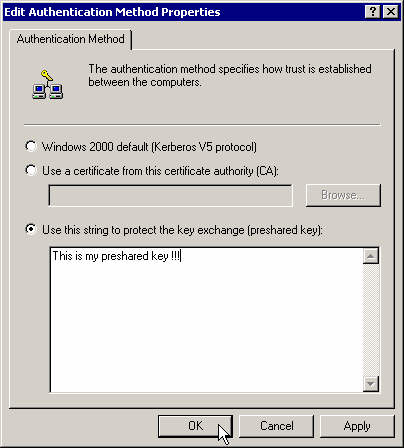
Close that rule's properties box.
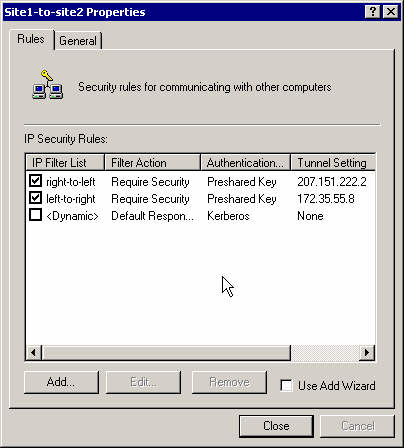
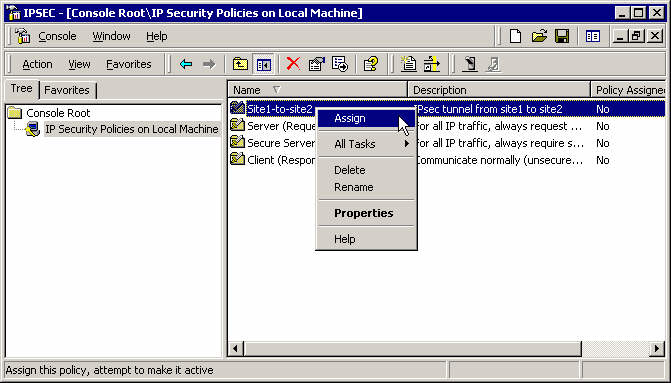
Select the 2 rules to apply on that policy.
On the general tab, click the Advanced button.
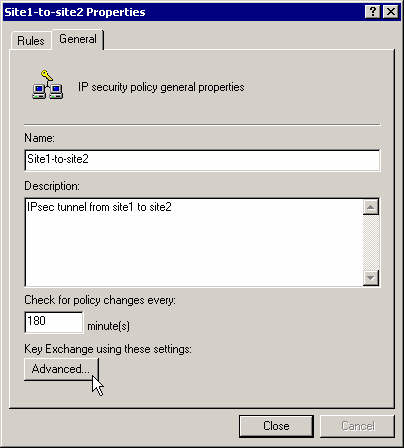
Select Master Key Perfect Forward Secrecy and click on the methods button.
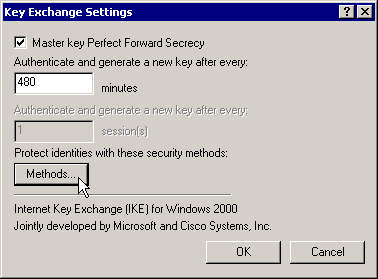
Move the proposal 3DES-MD5 to the top of the list and close that policy.
Assign that policy to make it active.
Test it. Wait and ping it again. Then check the events log because it never works the first time.
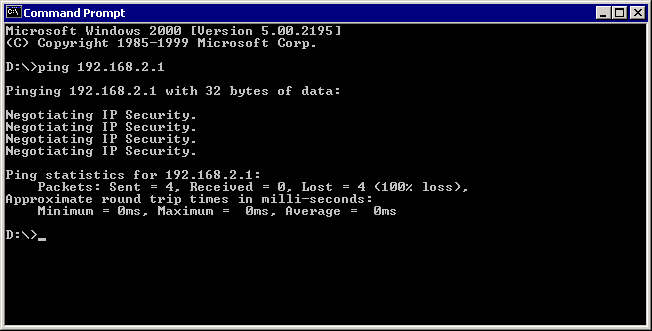
You'll have to modify your policy to correct whats wrong... restart the Ipsec service before testing again.
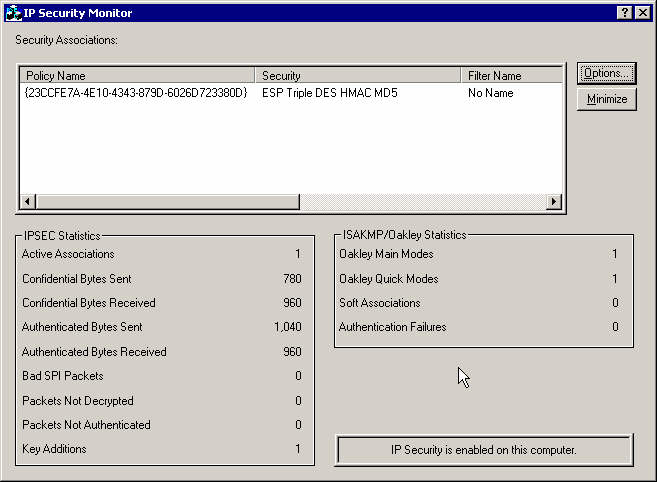
When it works you can monitor the tunnel with the ipsecmon program.
This was fun ;).